Data Leak Prevention - Behavioral Risk Management - Insider Threats
If you are a small to medium size business, SDAI can deliver you a full-featured solution to dramatically improve your security posture at the best price will find. Currently deployed all across Europe, Africa and Asia for government agencies, businesses and organizations alike, SDAI is the only company in Canada and South America certified to license, support and distribute SECURETOWER from FALCONGAZE. The solution is turnkey and can be deployed within days to start protecting your DATA from being exfiltrated from your enterprise and alerting you to risk exposures across your organization.
Data Leak Protection
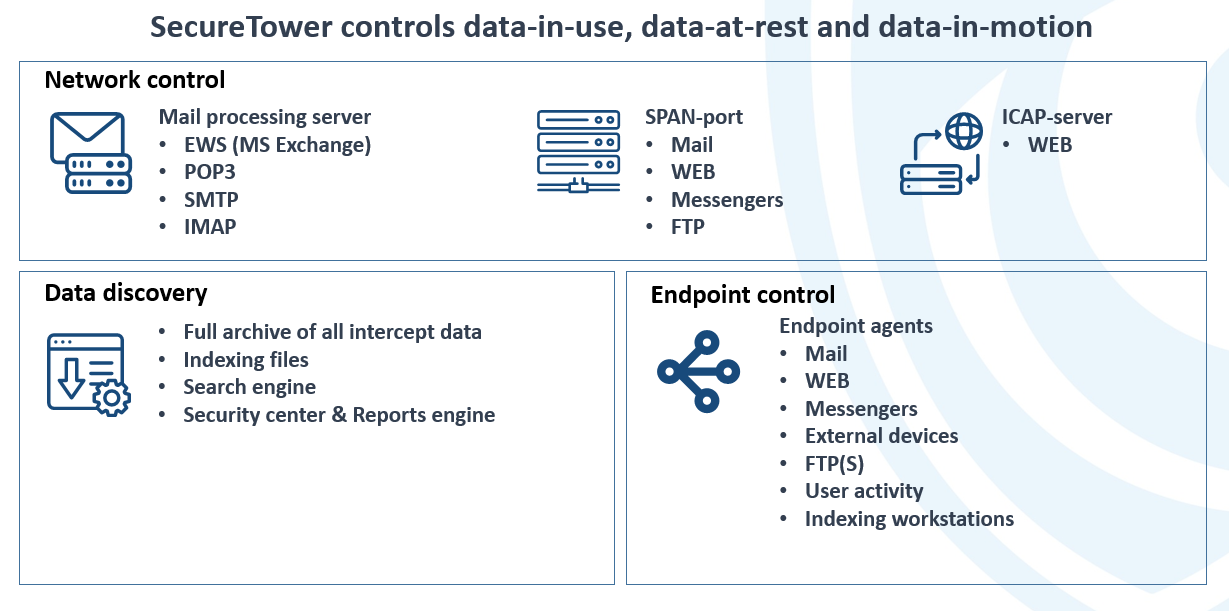
SecureTower is a complex and comprehensive tool for securing your company information resources, sensitive documentation, client and partner databases, commercial secrets, intellectual property and other crown jewel information under your protection. It provides control of a maximum number of communication channels, whether it pertains e-mail, messengers, social networks, cloud storages, USB, etc., thus minimizing economic and reputational risks.
SecureTower ensures not only timely investigation of incidents, but also their expedient resolution and prevention, by finding the source of the leak and allowing blocking as required, transfer of data or launch of undesirable processes. SecureTower won’t allow leakage of critical business information.
Using multiple types of data protection role, such as traffic interception and end point monitoring, it analyzes Network traffic or intercept directly on a work computer misuses of company assets. The software enables expansion of the number of channels intercepted by including the majority of messengers and internet-traffic under the encrypted HTTPS protocol. Depending on the customer’s needs, SecureTower allows the flexibility to combine multiple threat scenarios prevention roles.
How it works
The system analyzes all the data received and identifies incidents that warrant further investigation by the company units responsible for security issues. The analysis is based on applied sets of security rules which can be various and of any complexity. For instance, the system can notify when a large number of files is sent by the employees of the same department to print. It also can lock up the sending of documents containing confidential data from database by e-mail. All notifications about incidents are sent to the officer responsible who decides the matter.
Intelligence isn’t the tool itself. It’s what’s resides behind that makes the difference.
our edge

Behavioral risks management
User Behavior Analysis is a built-in feature of the system. It monitors abnormal and potentially dangerous behaviors within the organization and creates a risk analysis matrix for your Security Teams. It can automatically notify your Cyber Units of an impending breach.
How it works
This module automatically calculates employee risk level based on security rules. Then, it forms the list of all employees and their risk levels. Using filters and available data visualization settings, security officer can identify behavioral patterns unaligned with company policies. Changes and anomalies in employees’ behaviors are automatically displaying in a real time risk profile matrix. Risk analysis module collects all necessary information and generates reports required for immediate intervention or further investigations.
capabilities
Forms employees behavior patterns and assigns them the appropriate level of risk
Informs the security department about the level of risk and incidents of security policies that pose a real threat to the company
Divides incidents according to severity and allows Security staff to focus attention on the most important ones
Statistical reports and bright visualization reflect employees behavior changes in real time
Works from the moment of system installation. Likewise, it carries out a retrospective analysis (archival capabilities for forensic and HR investigation)
Behavioral Risk Analysis module allows transferring a security specialist from an incident response officer to a preventive manager. Thus, your security team can prioritize threats and make a decision to take action beforehand for successful threats responses.
INSIDER THREATS - FIND AND NEUTRALIZE
the basics

Insider Threats
Unfortunately, reports of significant security incidents have become commonplace. Whether large or small, enterprises today faces challenge to protect their clients, shareholders, and the public. Loss of sensitive data, be it personal information or intellectual property is fast-growing problem. And while most companies pride themselves on the loyalty and professionalism of their staff and contractors, reality is that life events and pressure from external sources can motivate even the most loyal insiders to assist in the exfiltration of data from your organization - sometimes with catastrophic results. In many instances, the reputation damage and defense costs have resulted in significant and enduring hardship for the affected enterprise.
SDAI - FALCONGAZE CAN HELP
DIGITAL FINGERPRINTS. The Software captures and analyzes network traffic including e-mails with sensitive attachments, it can monitor conversations and calls in IM, posts in social media, uploads and downloads from cloud storages, critical documents sent to USB devices and much more. All intercepted traffic and user activity data are saved to a database and analysed in real time, which makes it possible to intervene or investigate any incidents at any time. Using advanced security rules, SecureTower allows analyzes of corporate business processes and identify patterns that indicate a violation of the security policy.
SDAI partners will sit with you and your department leaders, understand your business and the challenges you are facing. After listening, and assessing you current mode of operations, SDA will propose a cost effective approach that will provide you with value immediately, …not 18 months from now. Whether you are heading a small, medium or a large enterprise, our “know how” and capabilities will serve, meet and most probably exceed your needs.
The SDA TEAM